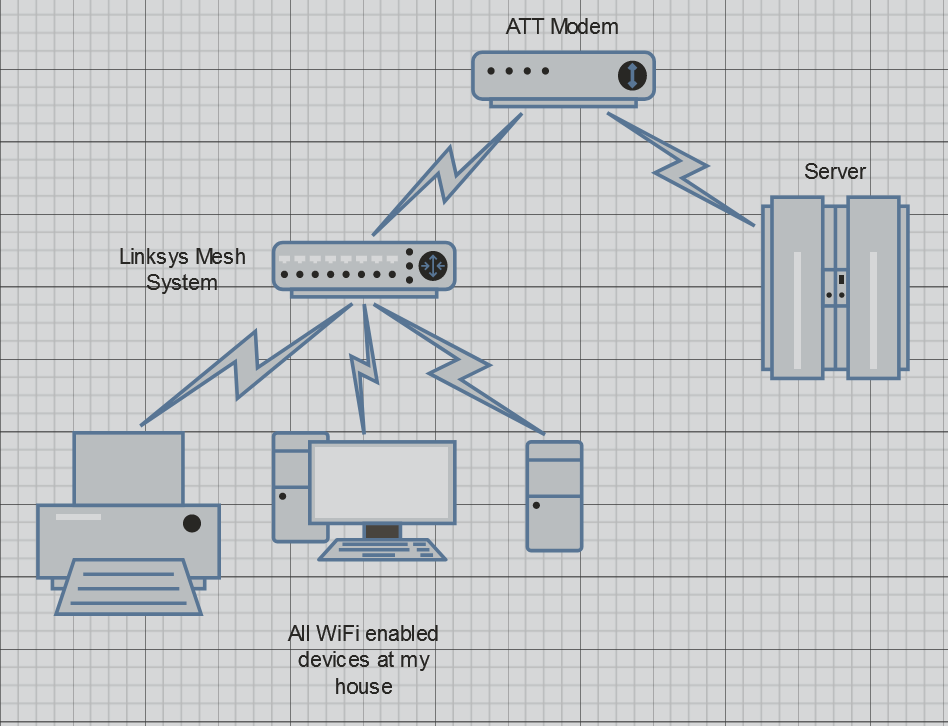
Hello all, I thought I would hop on and do a mid-year update of the server and some of the services.
Change Notes for Main Server
- All services now use Keycloak for authentication (with the exception of Vaultwarden and Guacamole)
- Mastodon, a federated social media platform has been added to the list of services
- Firefly iii, a manual financial management/budgeting tool has been added to the list of services
- Traefik is now the reverse proxy instead of Nginx
- A Postgres database has been added
So there have been quite a few changes, all of which I am very excited about! One of the most impactful ones in my opinion has been the addition of Keycloak for the sole reason of having one, singular log on for all applications. One surprise that came with it was the addition of “Passwordless” logins with their webauthn integration.
The webauthn integration allows for you to enroll any device as a Security Key. This allows you to use your phone or computer’s login system to log in instead of relying on a username and password. For some devices like a phone or tablet, this will allow you to use your phone’s fingerprint scanner or facial recognition feature to login. For PCs such as Windows 10/11 devices, you can use your TPM PIN code, facial scan or your login password. As a brief note, only newer computers support this feature. Your PC must be up to date. For MacOSX devices, your Keychain can be used to store your login information.
Another feature area I am excited to talk about is the reverse proxy change to Traefik. Previously, Nginx, a very popular webserver was used. However, as Keycloak got integrated into the stack, I found that being able to use Keycloak to authenticate users would be difficult, as such I settled on Traefik since it has really good support for using Keycloak in conjunction with it. It was a big change but much needed. Traefik offers a lot more extensibility than Nginx did. Although I will miss the simplicity of Nginx, Traefik will definitely hold up to the task!
One quick note on Vaultwarden before I close this section off, currently the developers are implementing single sign on that is compatible with Keycloak. This has been taking time due to the complexity of everything, but I am actively monitoring it.
Change Notes for Logging Server
- Logging server has been dockerized
Previously, I manually setup Graylog by manually installing everything. However early in the year, Graylog had a breaking update which seemed to break everything. After cutting my losses and starting fresh, I used a docker-compose file to setup a new instance of Graylog, Mongodb and memcached. Everything works well so far although I still haven’t rebuilt where I was before since the migration to Keycloak and Traefik took up a lot of time.
Change Notes for XOA Server
XOA (Xen Orchestra Appliance) is a web app used to manage Virtual Machines on the server. I used to use the default appliance that got installed with the system however I found that I needed all of the features, so I found a docker-compose file that builds and deploys the full one for me. The only downside is that I am responsible for updating the system, but that is ok with me.
New Servers
The only new server that has been added is the PXE Boot server. While this server is currently not used, I do have plans for it to be used to streamline updates to the virtual machines since I am on limited bandwith. The main idea is this: manually build a Debian based cloud-init image that is automatically set up to run a provided docker-compose file. Once the image is built, the newly built image will automatically be pushed to the Virtual Machines when they reboot next time.
Currently I am still in the implementation phase of this project. I have hit a few snags in the road with using Gitea and Jenkins in regard to how Gitea stores data. So this is on hold until the time being.
Future Plans for the End of the Year
- Setup Graylog fully
- Add OIDC to Guacamole
- Change Nextcloud to Minio
These ones are pretty much self explanatory. I would like to setup all of my rules in Graylog again so I can have a cohesive dashboard for traffic analysis and security purposes. Guacamole has yet to join the party on using Keycloak to authenticate however it is easy enough to do in an evening with a custom dockerfile. I have also been wanting to ditch nextcloud for quite a while and replace it with Minio. I don’t have much against nextcloud but I do think an S3 back storage solution would be better for hosting files than a PHP & Webdav backed solution. S3 storage solutions are pretty much the gold standard nowadays when it comes to storing files.
Closing Thoughts
Quite a lot of work has been done this year and I am very happy to see where everything is going! I might post periodic updates on my mastodon instance so make sure to follow me on mastodon: @kheestand@mastodon.heestand.tech
Thank you all and take care of yourself and others!